Cyber Security
Device, network and application protection from theft and damage of data and services.
Related articles

OAuth2 et OpenID Connect pour les microservices et les applications publiques (Partie 2)
Categories: Orchestration de conteneurs, Cybersécurité | Tags: CNCF, LDAP, Micro Services, JavaScript Object Notation (JSON), OAuth2, OpenID Connect
En utilisant OAuth2 et OpenID Connect, il est important de comprendre comment se déroule le flux d’autorisation, qui appelle l’Authorization Server et comment stocker les tokens. De plus, les…
By WORMS David
Nov 20, 2020

OAuth2 et OpenID Connect, une introduction douce et fonctionnelle (Part 1)
Categories: Orchestration de conteneurs, Cybersécurité | Tags: CNCF, Go Lang, JAMstack, LDAP, Kubernetes, OAuth2, OpenID Connect
La compréhension d’OAuth2, d’OpenID et d’OpenID Connect (OIDC), comment ils sont liés, comment les communications sont établies, comment s’architecture votre application et que faire des différents…
By WORMS David
Nov 17, 2020

Sécurisation des services avec Open Policy Agent
Categories: Cybersécurité, Gouvernance des données | Tags: Ranger, REST, Kafka, Autorisation, Cloud, Kubernetes, SSL/TLS
Open Policy Agent est un un moteur de règles multifonction. L’objectif principal du projet est de centraliser l’application de règles de sécurité à travers la stack cloud native. Le projet a été crée…
Jan 22, 2020

Authentification Kerberos et Spnego sur Windows avec Firefox
Categories: Cybersécurité | Tags: Firefox, HTTP, Kerberos, FreeIPA
Dans la mythologie grecque, Kerberos, aussi appelé Cerbère, garde les portes du monde souterrain pour empêcher les morts de partir. Il est communément décrit comme un chien à trois têtes ayant une…
By WORMS David
Nov 4, 2019
Apache Knox, c'est facile !
Categories: Big Data, Cybersécurité, Adaltas Summit 2018 | Tags: Ranger, Kerberos, LDAP, Active Directory, REST, Knox
Apache Knox est le point d’entrée sécurisé d’un cluster Hadoop, mais peut-il être également le point d’entrée de mes applications REST ? Vue d’ensemble d’Apache Knox Apache Knox est une passerelle…
Feb 4, 2019

Gestion des identités utilisateurs sur clusters Big Data
Categories: Cybersécurité, Gouvernance des données | Tags: Kerberos, LDAP, Active Directory, Ansible, FreeIPA, IAM
La sécurisation d’un cluster Big Data implique l’intégration ou le déploiement de services spécifiques pour stocker les utilisateurs. Certains utilisateurs sont spécifiques à un cluster lorsque d…
By WORMS David
Nov 8, 2018
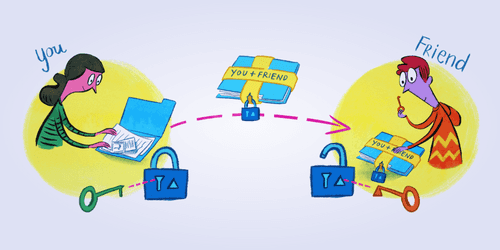
Guide pour les dossiers chiffrés sur Keybase
Categories: Cybersécurité, Hack | Tags: Cryptographie, Chiffrement, Système de fichiers, Keybase, PGP, Autorisation
Cet article est un guide sur l’utilisation des dossiers chiffrés de Keybase pour stocker et partager des fichiers. Keybase is un logiciel pour partager ses groupes, ses fichiers et ses messages. Son…
Jun 18, 2018

Apache Metron dans le monde réel
Categories: Cybersécurité, DataWorks Summit 2018 | Tags: Algorithme, NiFi, Solr, Storm, pcap, SGBDR, HDFS, Kafka, Metron, Spark, Data Science, Elasticsearch, SQL
Apache Metron est une plateforme d’analyse et de stockage spécialisé dans la sécurité informatique. La conférence a été présentée par Dave Russell, ingénieur en chef des solutions - EMEA + APAC chez…
May 29, 2018