Authentication
Authentication verifies the identity of the subject (user or program) which is performing by analysis of the identifier presented by the subject and confirmation of its authenticity. Authentication can be based on one or more factors:
- Knowledge: information the subject knows, such as a password or an
- answer to a special question.
- Possession: something the subject has, which could be a link, token, browser cookie, or a private key.
- Inherence: something the subject embodies, including biometrics such as fingerprints, voice or face recognition, retinal scans, movement patterns.
- Location: information about the place where the subject is physically.
Related articles
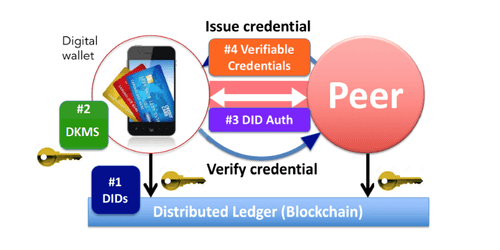
Self-sovereign identities with verifiable claims
Categories: Data Governance | Tags: Authentication, Blockchain, Cloud, IAM, Ledger
Towards a trusted, personal, persistent, and portable digital identity for all. Digital identity issues Self-sovereign identities are an attempt to solve a couple of issues. The first is the…
By Nabil MELLAL
Jan 23, 2019

Users and RBAC authorizations in Kubernetes
Categories: Containers Orchestration, Data Governance | Tags: Cyber Security, RBAC, Authentication, Authorization, Kubernetes, SSL/TLS
Having your Kubernetes cluster up and running is just the start of your journey and you now need to operate. To secure its access, user identities must be declared along with authentication and…
Aug 7, 2019

Connecting to ADLS Gen2 from Hadoop (HDP) and Nifi (HDF)
Categories: Big Data, Cloud Computing, Data Engineering | Tags: Hadoop, HDFS, NiFi, Authentication, Authorization, Azure, Azure Data Lake Storage (ADLS), OAuth2
As data projects built in the Cloud are becoming more and more frequent, a common use case is to interact with Cloud storage from an existing on premise Big Data platform. Microsoft Azure recently…
Nov 5, 2020

Keycloak deployment in EC2
Categories: Cloud Computing, Data Engineering, Infrastructure | Tags: Security, EC2, Authentication, AWS, Docker, Keycloak, SSL/TLS, SSO
Why use Keycloak Keycloak is an open-source identity provider (IdP) using single sign-on (SSO). An IdP is a tool to create, maintain, and manage identity information for principals and to provide…
By Stephan BAUM
Mar 14, 2023

Buttercup to KeePass exporter
Categories: Cyber Security | Tags: Authentication, CSV, Node.js
Buttercup is a password manager which works on all major platforms including Linux, macOS, Windows, iOS and Android. On March 3rd, Buttercup’s main contributor Perry Mitchell announced the retirement…
By David WORMS
May 14, 2025